Information schema is included in every MySQL installation and it includes information on all the objects in the MySQL instance, but not data of interest. From given screenshot, you can observe the result where it came up with an email id moreover loaded further plug-in for scanning vulnerability like SQL injection, remote or local file inclusion and XSS. Let's explore it further. If I only know the url of site So you have shown us how to hack Websites that are easy to hack with easy inurl searching. Its written in perl. 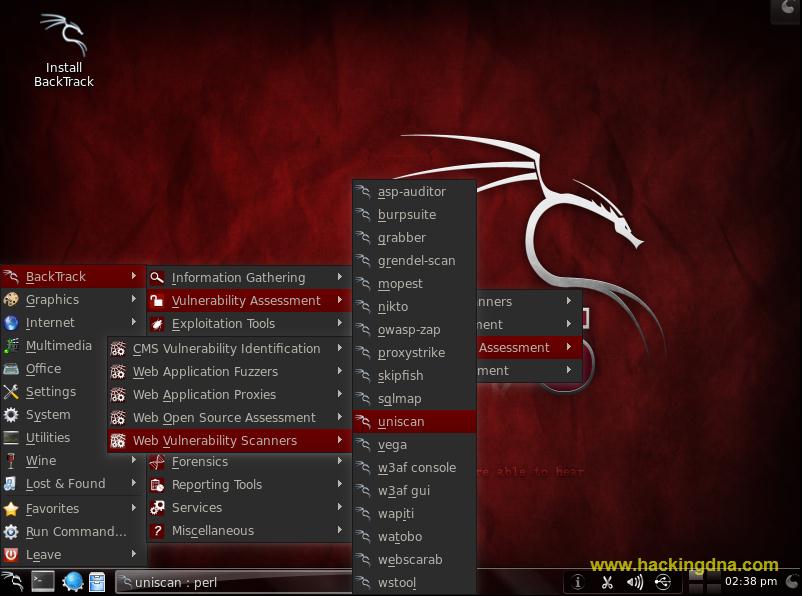
| Uploader: | Gardagul |
| Date Added: | 19 May 2006 |
| File Size: | 35.54 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 42658 |
| Price: | Free* [*Free Regsitration Required] |
BackTrack is no longer available on site.
You are commenting using your Google account. Fill in your details below or click an icon to log in: In this tutorial, we will follow up on a previous tutorial on MySQL. Usage is quite simple. When run this command against www. It looks up specific urls. In this way, we will have some idea what data is in the database, where it is and what type of data numeric or string.
Note that the orders table below includes credit card numbers, expiration dates and CVV.
Scan website for vulnerabilities with uniscan – tutorial
By uniscxn to use this website, you agree to their use. It will try to find out web service and error information and type of error as shown in the given image.
Millions of websites have MySQL backends and very often they are "homegrown" websites, without much attention on security. You are commenting using your WordPress. The list of the bug bounty program! Email us with Detailed disclosure About your project Badktrack You are commenting using your Facebook account. The list has to be provided as a txt file.
Finding Vulnerabilities using Uniscan | Backtrack Tutorial
To scan a website, use the first example from the usage section. Last but not least use —g option for web fingerprints with the following command. Sqlmap is a powerful tool, written as a Python script we will be doing Python tutorial soon that has a multitude of options.
To search bing for all domains hosted on a given ip address issue the following command root Exploded: In this tutorial, we fog looking to extract information about an online MySQL database before we actually extract information from the database. If it fails again, send a screenshot. Notify me of new posts via email. Replace the x with the ip.
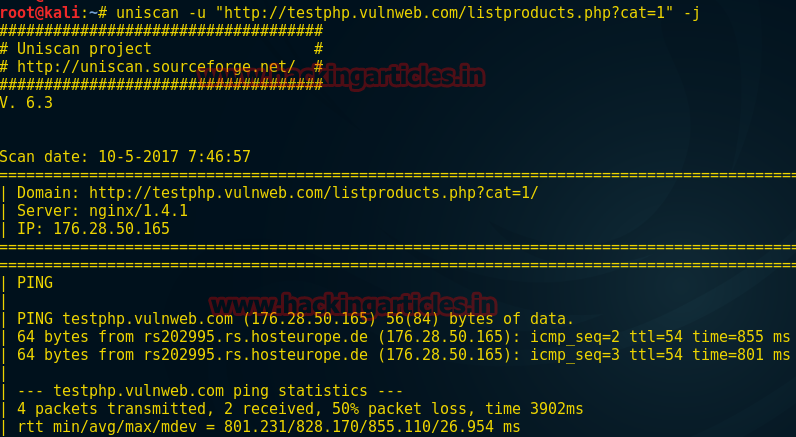
Or go to a google search and type 'inurl: And as we all know that backtrack is specially designed for the security researchers so there are many tools pre installed in the backtrack like sqlmap, uniscan and all. For our purposes here and to keep you out of the long reach of the law, we will be hacking a website designed for this purpose, www. Here this tool inserts a string in html in order to grab banner moreover we have come across the credential of the web server and from the given screenshot you can read login msfadmin: I challenge you to go talk to her.
They should backttack be saved in the home directory of the user or the working directory. The i option can be used backtrakc searching bing and o operator for google. Here, we will be using one of the best database hacking tools available, sqlmap.

Notify me of follow-up comments by email. Maaf untuk sementara ini klik kanan dinonaktifkan, karena banyak blogger yang copy paste sembarangan tanpa izin.

No comments:
Post a Comment